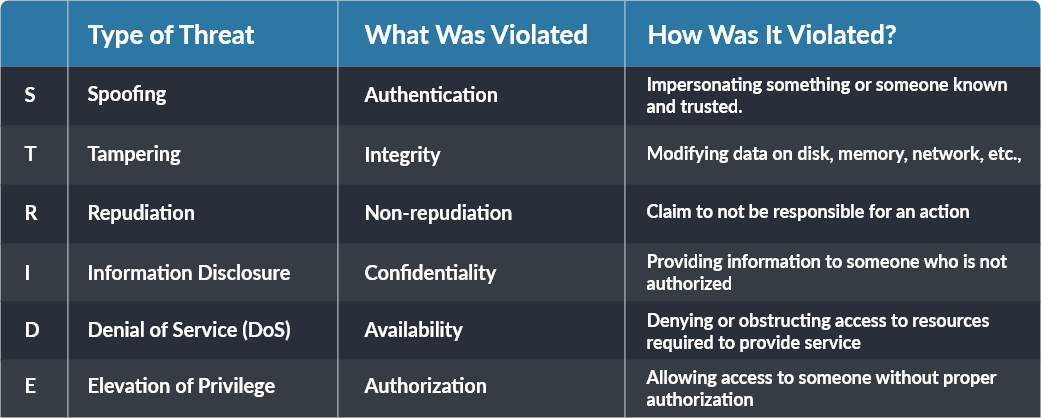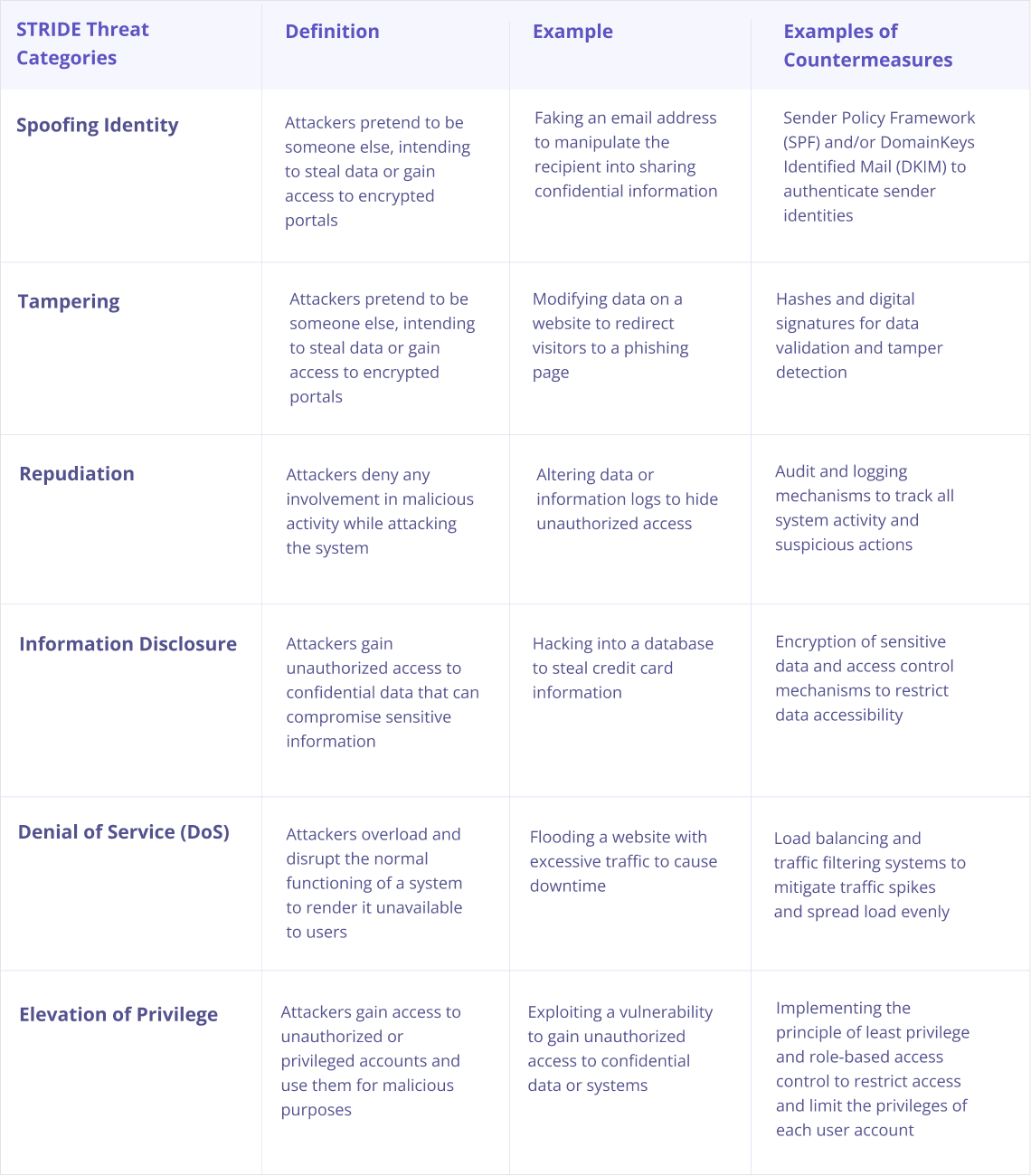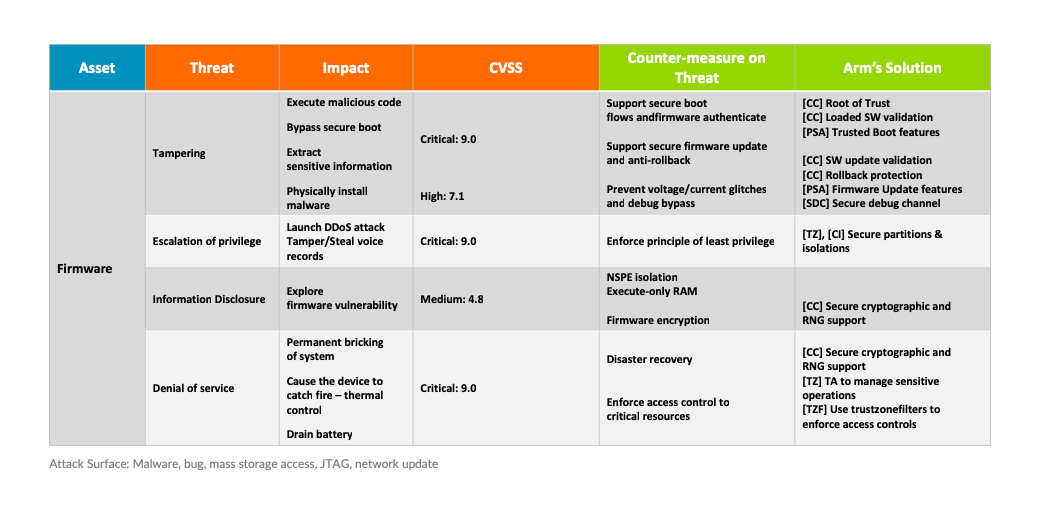
Five Steps to Successful Threat Modelling - Internet of Things (IoT) blog - Arm Community blogs - Arm Community

Sensors | Free Full-Text | Robust Stride Segmentation of Inertial Signals Based on Local Cyclicity Estimation
![PDF] A STRIDE Model based Threat Modelling using Unified and-Or Fuzzy Operator for Computer Network Security | Semantic Scholar PDF] A STRIDE Model based Threat Modelling using Unified and-Or Fuzzy Operator for Computer Network Security | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/c38ea87c76d6aa5afaa8311f592bc3daf5a4d7c2/2-Figure1-1.png)
PDF] A STRIDE Model based Threat Modelling using Unified and-Or Fuzzy Operator for Computer Network Security | Semantic Scholar
)